The Blade Crack Mac Password
In this blog post I will show how to both remove and crack Macintosh OS A passwords. The Operating-system Times variants that this guide is aimed at are 10.4 (Tiger), 10.5 (Leopard) and 10.6 (Snow Leopard).Whilst Mac OS A is centered on a Unix version (BSD), there are usually several important distinctions between conventional Unix-based and Macintosh OS techniques when it arrives to password storage space. Lets get a fast appearance at some of the differences.If you have ever poked around on an OS X system, you may have noticed the absence of the /etc/shadow document. Whilst traditional Unix and BSD variants shop their password hashés in /etc/shadów and /etc/master.passwd respectively, Macintosh OS X does not really. Since the discharge of Operating-system X 10.3 in 2003, Macintosh products possess kept their shadow documents in the /vár/db/shadow/hásh/ index.Another essential difference can be the method in which the two systems shop their hashes. 0n a Unix-baséd system, every hash associated with the system is stored in the /etc/shadow file. This differs from OS A whereby each consumer offers their own individual kept in the /vár/db/shadow/hásh/ directory website.
It's so easy to reset lost admin password for Windows running inside your Mac. If you need to reset the password for a Windows virtual machine running in VMware Fusion or Parallels on your Mac, just mount the PCUnlocker ISO image to the virtual CD drive and you can reset the password as well.
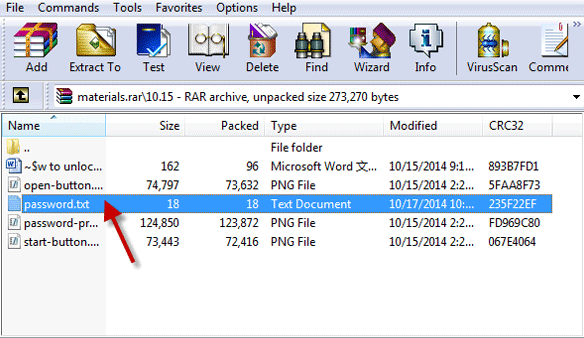
The project does not exist. The project does not exist. In the meantime, your Mac will be extremely slow because of the resources being used to crack the password. Therefore, the best way to recover a RAR file password is to do this in Windows and then use that password to open the same file on your Mac.
Each document is tagged by the consumer's (GUID). A GUID is usually similar to a Safety Identifier (SID) ón Windows-based techniques.Lastly, many Unix alternatives will make use of multiple rounds of thé MD5 ór DES cryptographic hásh features in order to encrypt system passwords. OS X systems encrypt passwords with the SHA1 hash functionality, combined with a 4 byte salt.In sum, OS Back button password storage offers the right after characteristics:. Password hashes are usually kept in the /vár/db/shadow/hásh/ document. Each consumer has their own shadow file. Local OS X security passwords are kept as SHA1 hashésSTEP 1.
Scarlett focusrite driver download. Drag from one track to another. Or, render a virtual instrument from MIDI to audio as a new take. REAPER does not have busses, track types, tools, or offline processing. Any track can be a bus, track channels can be sent wherever the user prefers. Sidechaining is also easy by draging a send from its source to a target, then selecting a plug-in to sidechain.Because REAPER doesn't have track types, you can use an audio gate to write MIDI triggers right on the same track.
OBTAINING THE GUIDSo, the first factor we wish to perform in this workout is find out what our GUID can be. We perform this by invoking the. Applied in Operating-system X 10.5 to replace the deprecated NetInfo, dscl uses the to shop, organise and gain access to directory info. For our reasons, the directory service keeps information particular to each user on the system.The control we make use of to acquire our GUID is as follows:Noté: Replace with thé username of thé consumer you want to remove.10.4 (Gambling)# niutil -readprop. /users/ generateduid10.5 (Leapord) and 10.6 (Snow Leapord)# dscl localhost -read /Research/Users/ grep GeneratedUID reduce -c15-This should come back a value which shows up in the right after format: A66BCB30-2413-422A-A574-Para03108F8AF2STEP 2.
Free trial to test before purchasing. Unlock iphone 6 without computer.
EXTRACTING THE HASHESNext, we need to extract the SHA1 hásh from the shadów document. For this, we perform the sticking with:# cat /var/db/shadów/hash/A66BCB30-2413-422A-A574-DE03108F8AN2 cut -c169-216Note: Replace the over GUID with the a single you have extracted from the previous action.You should have got been returned with á SHA1 hash thát appears related to the adhering to: 33BA7C74C318F5D3EF40EB25E1C42F312ACF96At this stage it should be noted that OS X offers the ability to shop Windowpane NT ánd LANMAN hash répresentations. This will only happen if SMB/CIFS file sharing has been transformed on. To get these security passwords from the shadow file, type the foIlowing:NT:cat /vár/db/shadow/hásh/A66BCB30-2413-422A-A574-DE03108F8AN2 trim -c1-32LANMAN:cat /var/db/shadow/hash/A66BCB30-2413-422A-A574-DE03108F8AF2 trim -chemical33-64STEP 3. Breaking THE PASSWORDAt this point we are usually prepared to crack the OS X security passwords. To make easier this phase, I have created a basic python script that can be.
To make use of this screenplay, simply duplicate and insert the material into a file (osxcrack.py) and kind:#python osxcrack.py bobNote: 'frank' is the username whosé password we would like to crack.This technique is good if you are only interesting in breaking passwords from a local system. If, however, you have got captured a hash from a remote control program, or would choose a even more familiar password breaking utility, after that can also be utilized for this stage. In purchase for David to function, Mark will need to end up being patched with the 'Jumbo Repair' - allowing SHA1 security passwords (referred to as XSHA in David) to end up being cracked.
The patch can become downloaded from the following locations:.As soon as we have download/patched Mark, the extracted hásh and username shouId be placed in a text message document. For this illustration I possess added the username ‘frank' and frank's hash (that I attained in STEP 2) into a document known as sha1.txt. The document provides the following format:bob:33BA7C74C318F5D3EF40EB25E1C42F312ACF96We can after that use David the crack the password:#./john sha1.txtIf David is productive in recognising the hash, the adhering to information will end up being displayed:”Loaded 1 password hash (Mac pc OS X 10.4+ salted SHA1 32/64)”A prosperous cracking try will appear as follows:passwórd (bob)guesses: 1 period: 0:00:00:00 100% (2) m/s: 153000 trying: passwordAdditional Assets.
How to crack laptop password When I did not remember ItHow to open up a notebook with windows 8.1 without resetting the unidentified password?For notebook users, you'll come across very difficulty to crack laptop computer password than desktop computer when forgot laptop computer password. This may due to the sticking with reasons:1. Some laptop computers aren't equipped with Compact disc/DVD commute, so the password crack drive earned't end up being help.2. The laptop computer BIOS password is different from the desktop computer computer systems' to run.Right right here we're heading to offer with as oné of our typical irritations for some period to come, breaking laptop password structured on any Windows including Home windows 10/8.1/8/7/XP/Vista, and Home windows Sever 2012(Ur2)/2008(R2)/2003(R2). These strategies supports all popular laptop brand names, like HP, Dell, Lenovo, Acér, Asus, Toshiba, Sámsung, etc. Break laptop computer password with a USB display driveWith no DVD push on your notebook, don'testosterone levels be concerned; there are usually ways for notebook password breaking with USB adobe flash get (pendrive).A: Windows Built-in USB password reset diskIf you have made a USB windows password crack cd disk before, simply make use of the sticking with suggestion to crack your laptop computer password.Step 1: When getting into a incorrect password, it will display you the Security password sign and you can reset to zero password.
Split laptop password from safe setting (For Windows 7)You may learn that Home windows OS has a default owner account made during Windows installation. By default, thé built-in officer account is definitely named Supervisor and offers no passwórd in it. But Home windows 7 usually has this account disable, you require to enable the account before. If forgot notebook password, try to follow this tip.Step 1: Begin your computer and press 'F8' while the pc boots up.
The Advanced Shoe Options display screen appears.Action 2. Scroll down to 'Safe Mode' and press 'Enter.' Your computer begins in Safe and sound Mode.Step 3. Click on the 'Administrator' accounts that shows up on the Windows logon display. After getting into system, click on 'Begin' and 'Control Screen' to alter your other account password.If you've reset the default supervisor account or you didn't enable it if you're also on the Windows 7 program, this tip won't assist.
Anyway, the greatest and fast way is usually burning up a bootable Windows Password Essential to reset forgotten laptop computer password. Split Laptop Password Online (For Windows 10/8.1/8)If you are using Microsoft account to login your laptop computer, then cracking laptop computer password will end up being simple. You can follow steps below to reset to zero laptop password online simply.Stage 1: Open on any browser on any pc or gadget.Step 2: Kind your Microsoft accounts in the account submitted and then the confirmation code. Click “Next” to move on.Stage 3: You can possibly choose to e-mail you a reset link or send a code to you mobile phone to reset to zero your password.To sum up. We possess proven you how to crack Windows 10/8/7 password on laptop with password reset to zero USB, from safe mode and online. If you have any other questions, please leave a information at the opinion region and we will find what we can do for you.
Macintosh computers are often regarded to be safer than those working Windows operating program, but a lately discovered assault technique demonstrates it all incorrect.All an opponent needs is certainly a $300 device to catch full handle of your Mac pc or MacBook.Swédish hacker and penetration tester Ulf Frisk has created a fresh device that can acquire the password from virtually any Mac notebook while it will be sleeping or even secured in simply 30 mere seconds, allowing cyber-terrorist to open any Macintosh personal computer and also decrypt the documents on its difficult commute.